You might've heard that HTTPS is a way to secure your website using an SSL certificate. Have you wondered what makes it secure? What goes under the hood when your browser communicates to the server? Let's find out!
What is SSL/TLS?
SSL is an encryption protocol developed by Netscape. Yes, the company which developed the world's first web browser. SSL was changed to TLS after SSL version 3.1 which indicated that it is no longer associated with Netscape. So we can say that TLS is just the updated version of SSL being used. These days SSL and TLS are being used interchangeably.
HTTPS uses the TLS protocol to encrypt the communication which happens between the browser and the webserver.
What does TLS do?
TLS ensures the following two things
- Your data is protected from being tampered with during communication.
- Your data is sent and received from the right source.
This makes it difficult for an attacker to read or modify the information you send or receive (like your bank details).
How does TLS work?
TLS mainly has two steps
- TLS Handshake
- The actual data transfer process
We'll go into detail about these two processes. Before that, we need to understand what is encryption and what are its types.
What is Encryption? 🔒
In simple terms, encryption is basically scrambling the data so that only the person intended can understand it.
Let's say you have a data "ABC" which you want only your friend to read. But you also have another friend who's snooping over your conversations. You and your friend decide on a secret code - "two turns left" which only you both know (we'll look into how to send this secret code as well).
Instead of sending "ABC" you now send "CAB". Now because of the secret code, they know that the data has been rotated circularly to the left twice. So they can easily decrypt it by turning it to the right twice to get the original message. That's how encryption works! The secret code you used is referred as a key 🔑 in the cryptography world.
Obviously, in a real scenario complex algorithms are used to scramble the data or even add some dummy data in between for encryption. But this is the gist of how it works.
There are two types of encryption
- Symmetric encryption
- Asymmetric encryption
In symmetric encryption, the encryption and decryption process is done using the same key at both ends. The above example was done using symmetric key encryption because you and your friend shared the same key "two turns left" for encryption and decryption.
In asymmetric encryption, there are two keys on each side.
- Private key
- Public key
The public key is publicly available to anyone. But your private key should be kept a secret. Because of this, asymmetric encryption is also called public-key encryption.
Keep the following two points in mind:
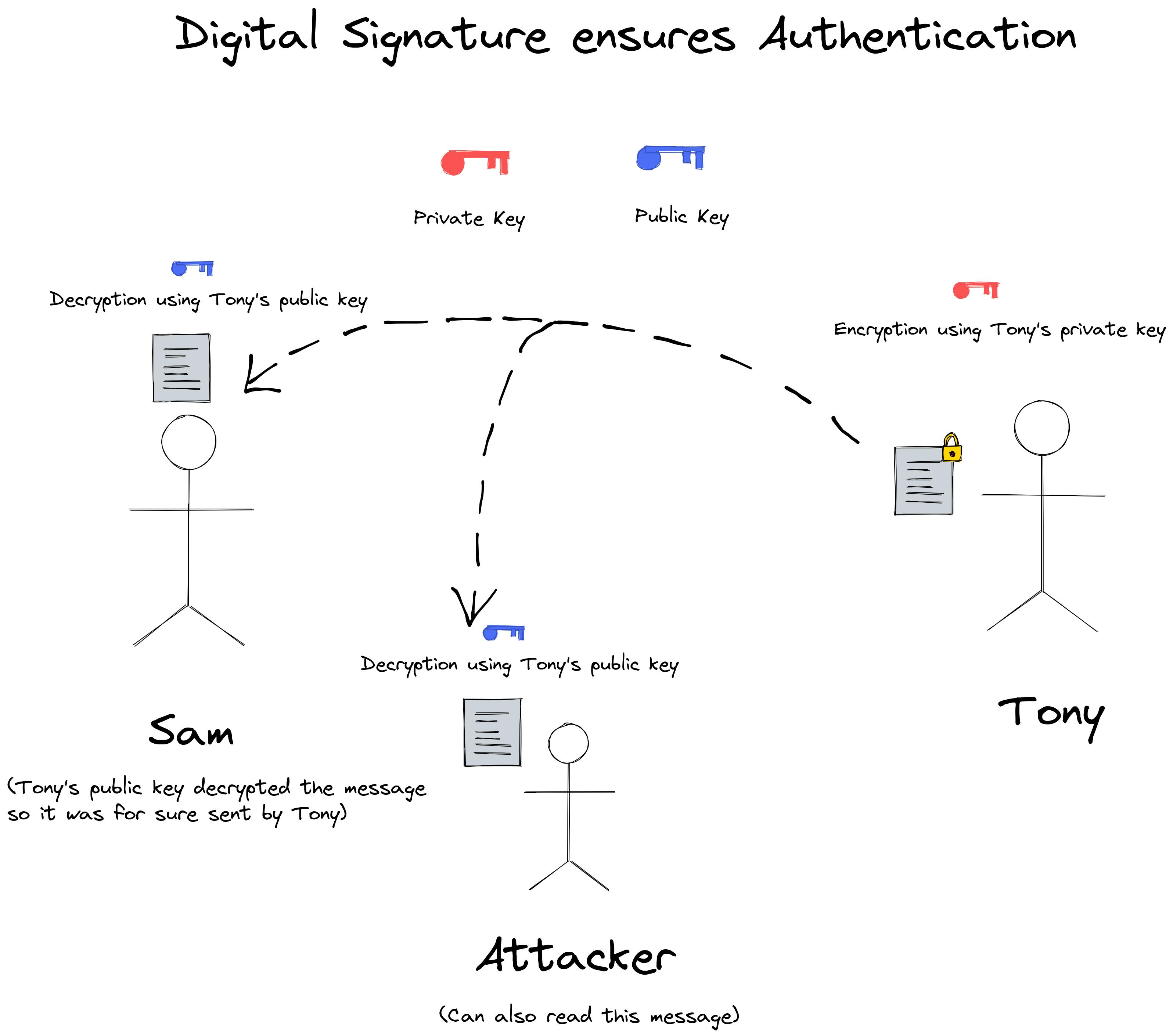
The private key is used for encryption and the public key is used for decryption when we want to authenticate a user i.e. to know who the user is. This is also known as Digital Signature. It is similar to how physical signatures work. You sign a document and say this document is verified by me. This does not prevent anyone from reading the document.
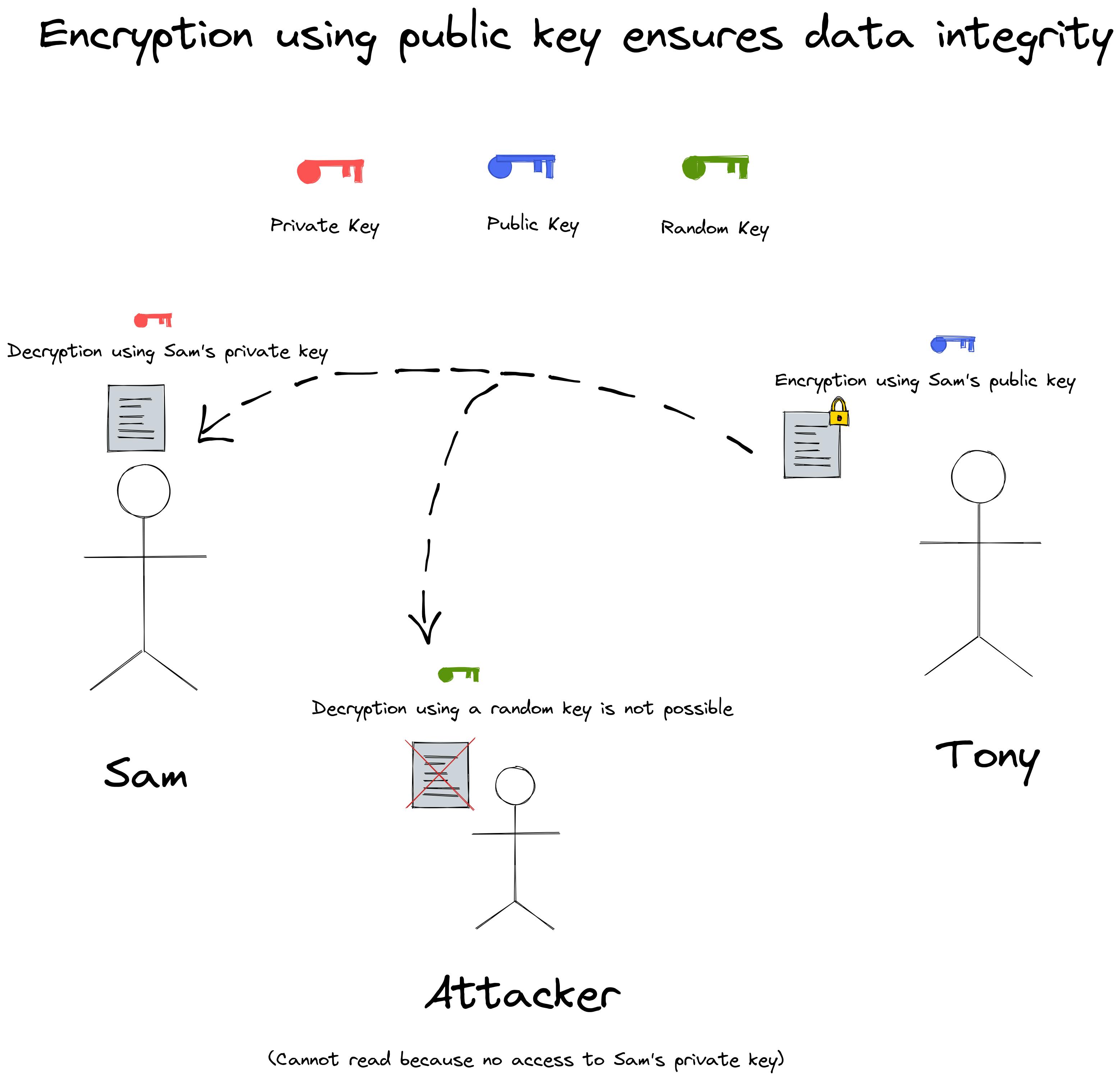
The private key is used for decryption and the public key is used for encryption when we want to ensure the integrity of the data i.e. to avoid reading or modifying the data. This is similar to the door locking mechanism. You can lock a door using a lock that could be available to anyone. However, only the person with the key to the lock can unlock it.
Encrypting with the private key does NOT ensure that your data won't be snooped over by an attacker. This is because they have your public key to decrypt it. However, the public key can only decrypt data that has been encrypted by its corresponding private key pair. This would only help us in checking if the data has been sent by the correct source because if it did, then the sender's public key that you have would be able to decrypt the data.
Now let's get back to TLS starting with the TLS Handshake.
What is TLS Handshake?
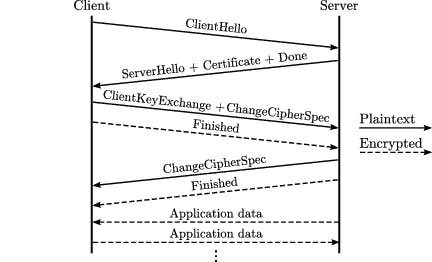
TLS Handshake uses asymmetric encryption to generate the session keys for the data transfer process. During this process, four session keys are generated. Session keys play an important role in the data transfer process.
How does the TLS handshake happen?
There are three parts involved in the handshake.
- client random: This is a random string generated by the client.
- server random: This is a random string generated by the server.
- premaster secret key: This is a secret key usually generated by the client.
The client random is encrypted by the client's private key and sent to the server.
The server random is encrypted with the server's private key and sent to the client.
The client and server random are only used for authentication purposes so we don't need to encrypt using the public key to protect their readability.
The pre-master secret is encrypted with the server's public key because we don't want this to be exposed. The server's public key is available to the client via the SSL/TLS certificate.
credits - researchgate.net
If we only use the pre-master secret, we would be prone to man in the middle attack because the pre-master secret could also be generated by an attacker acting as a client. Without the client random, there would be no way for the server to verify if it actually came from the client.
Now both client and server have a copy of client random, server random, and the pre-master secret key. Both of them combine it using a predecided algorithm which results in the same master key being generated on both sides.
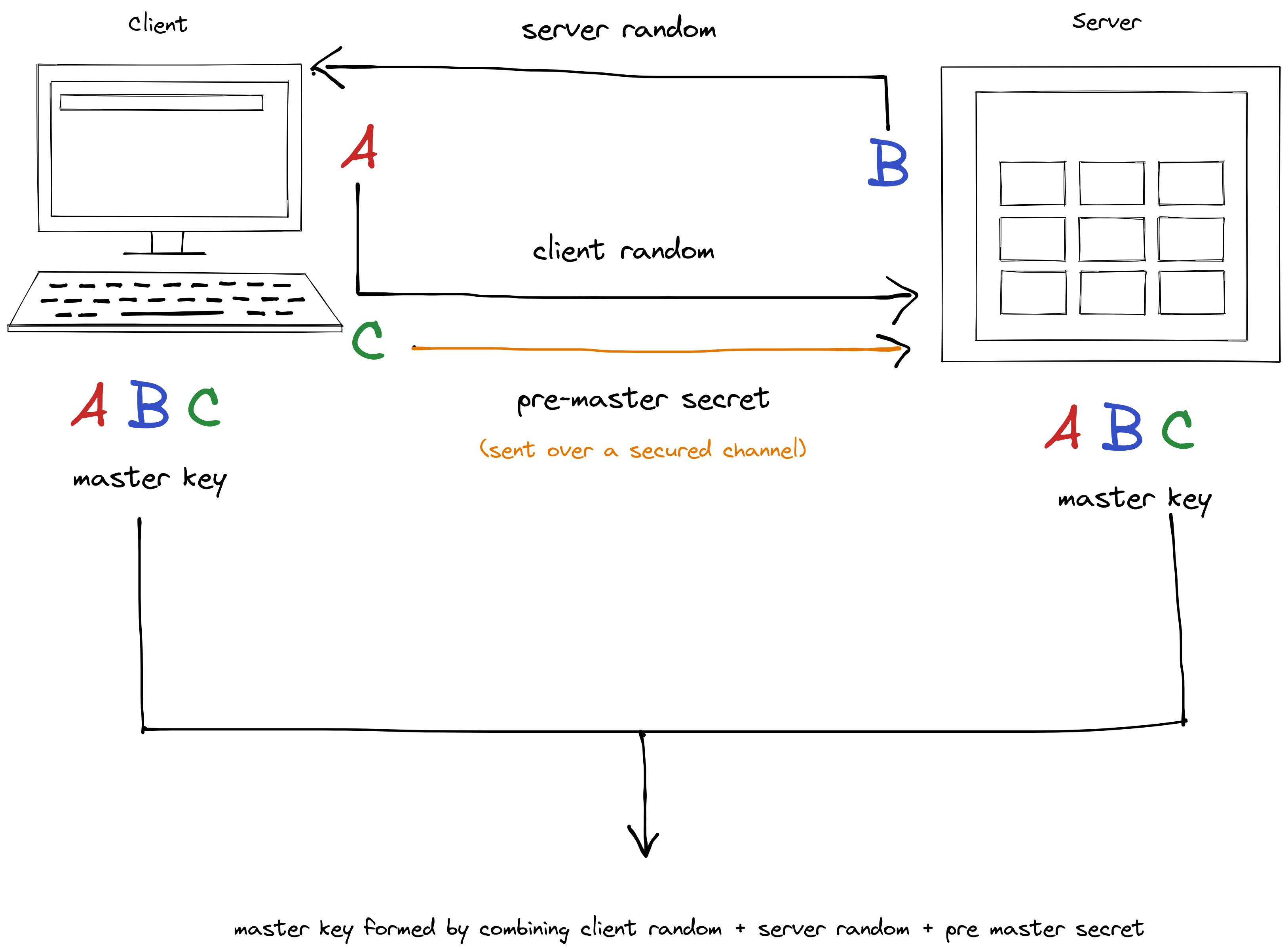
Using this master key, both client and server generate the four session keys for the data transfer process on both ends. As both of them use the same master key, the four session keys generated would be the exact same on both ends.
The actual data transfer process
The data transfer happens using the HTTPS protocol which is a protocol meant for sending data over the web.
These are the four session keys generated during handshake:
- client write key
- server write key
- client write MAC key
- server write MAC key.
As we mentioned that the same keys are generated on both ends, does that ring a bell?
Yes! During the data transfer, symmetric encryption is used.
The client uses the client write key to send its data to the server. The server decrypts the data using its copy of the client write key to retrieve the data. This ensures the integrity of the data.
The client digitally signs the data using the client write MAC key and the server verifies the data if it came from the right source using its own version of the client write MAC key.
Similarly, the server uses the server write MAC key and write key to authenticate and encrypt the data it sends to the client.
That's how data transfer works between a client and server using HTTPS and SSL/TLS protocols.
If a site uses HTTP, it means there is no implementation of the data encryption and an attacker could easily read your data or even modify it. That's why it is very important to use only the sites which have HTTPS enabled (browsers show this using a padlock sign in the URL bar.)
Thanks for the read. Follow me for more such articles!
Post your comments/feedback down below 👇
Ciao! 👋